The United States Computer Emergency Readiness Team (US-CERT) and the U.S. Department of Homeland Security sponsor a database of common vulnerabilities and exposures (CVE). These CVEs have been widely adopted as a way to describe and reference known vulnerabilities.
Each CVE entry contains a standard identifier number, a brief description of the security vulnerability, and any important references to related vulnerability reports. The CVE list is maintained by a not-for-profit, the MITRE Corporation, on its public website.
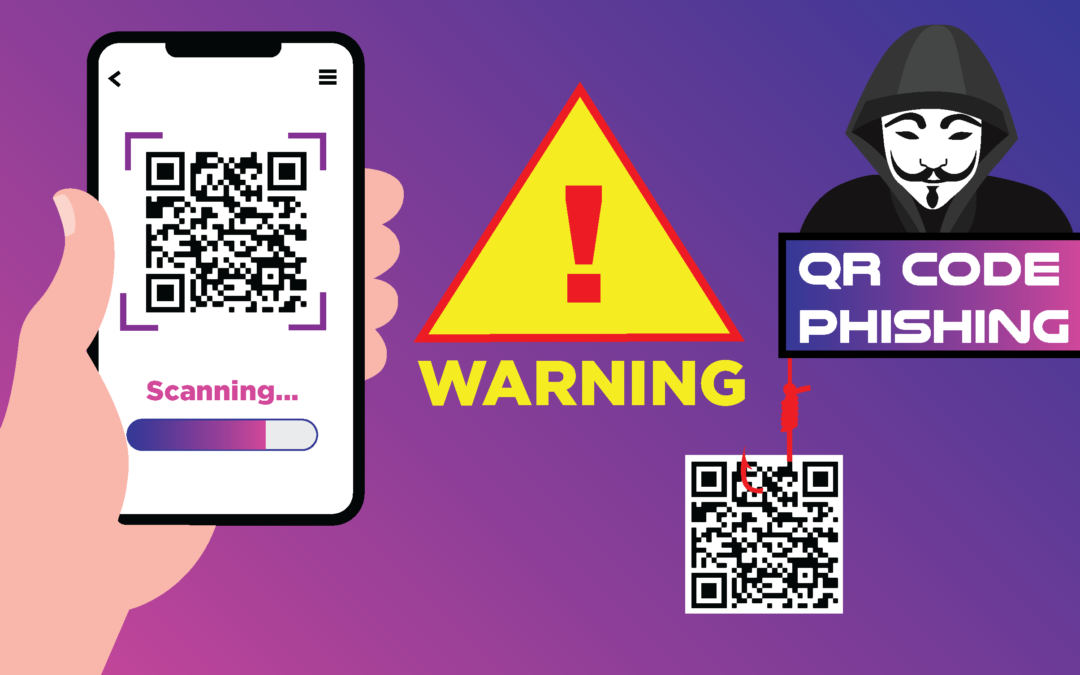
The Dark Web
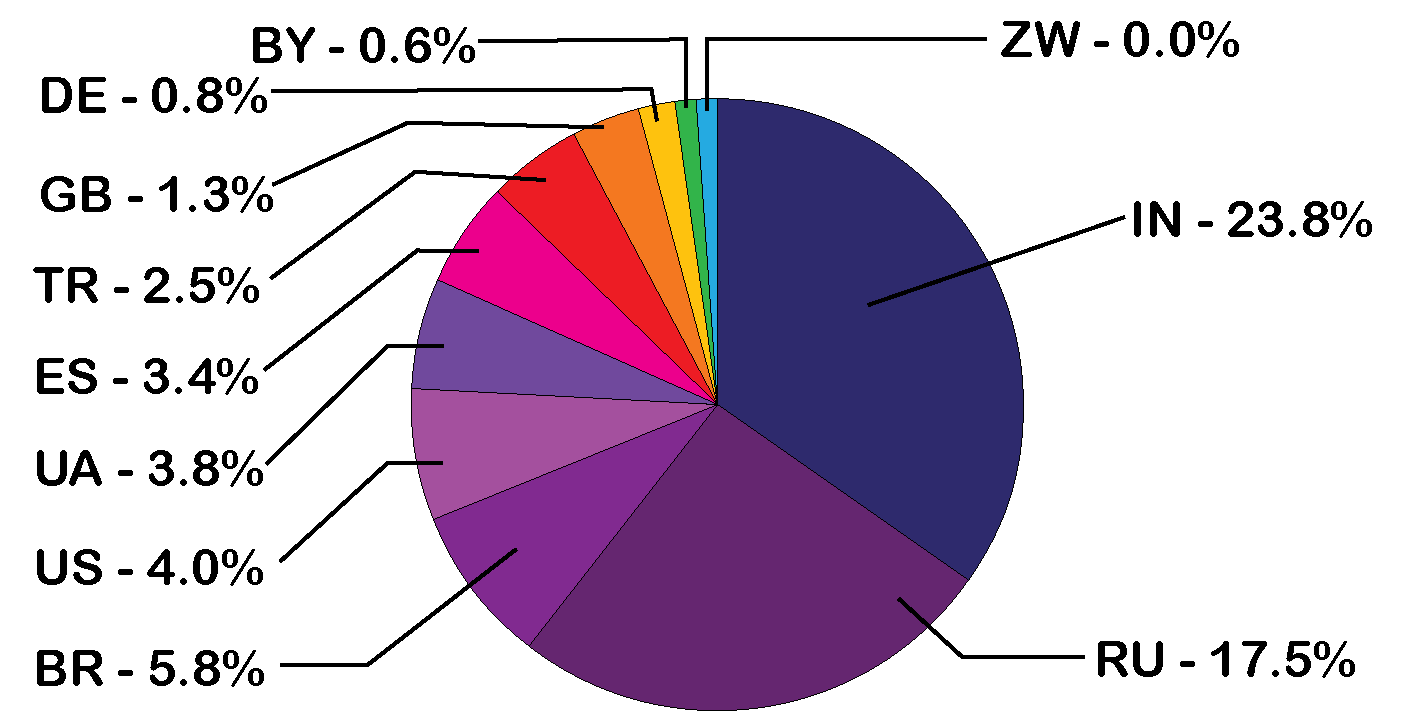
This refers to encrypted web content that is not indexed by conventional search engines and requires specific software, authorization, or configurations to access. Expert researchers monitor the dark web for new threat intelligence.
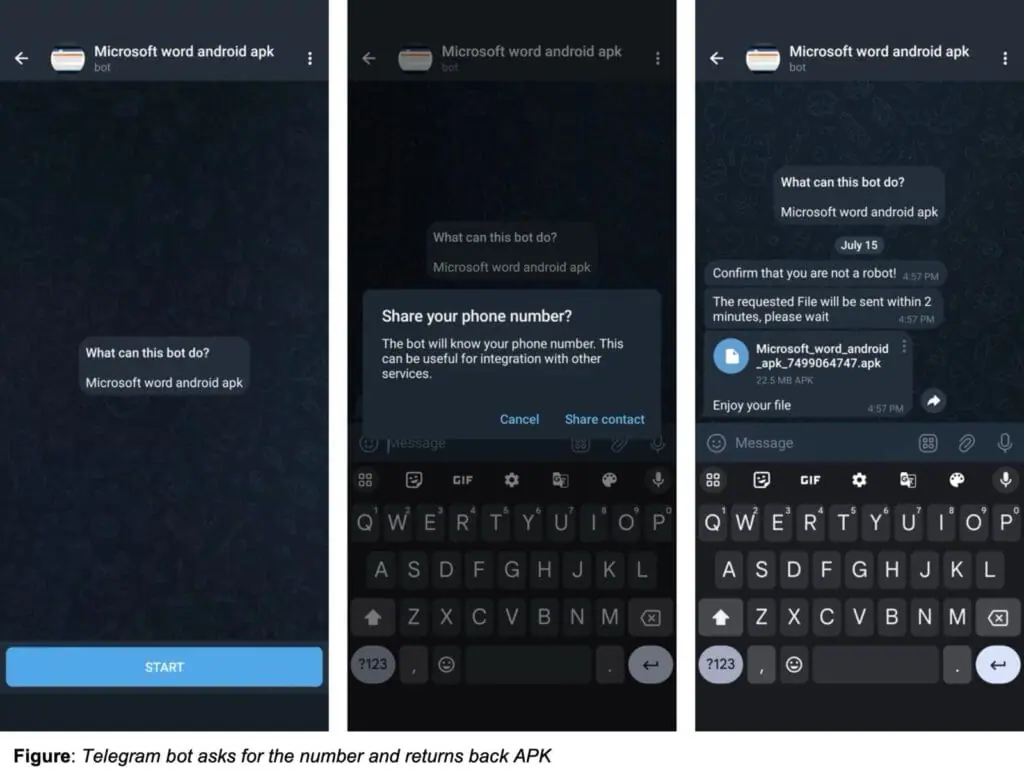
Indicator of Compromise (IOC)
IOCs such as malware signatures or malicious domain names provide evidence of security breaches and details about them.
Automated Indicator Sharing (AIS)
Automated Indicator Sharing (AIS), a Cybersecurity and Infrastructure Security Agency (CISA) capability, enables the real-time exchange of cybersecurity threat indicators using a standardized and structured language. Structured Threat Information Expression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII) are standards used in AIS.