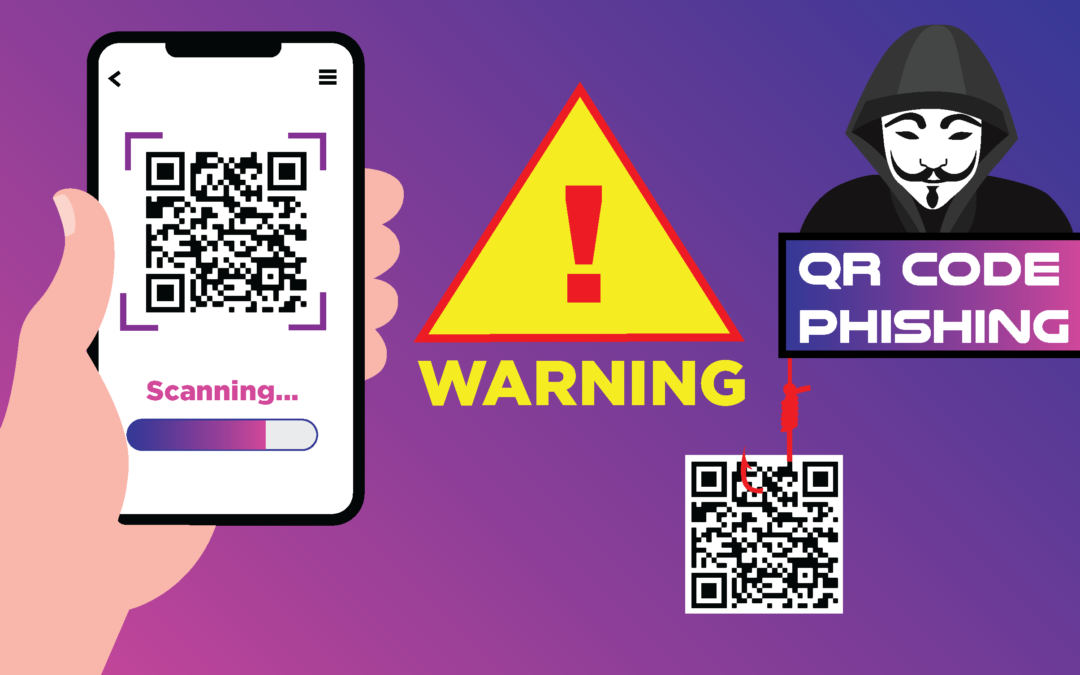
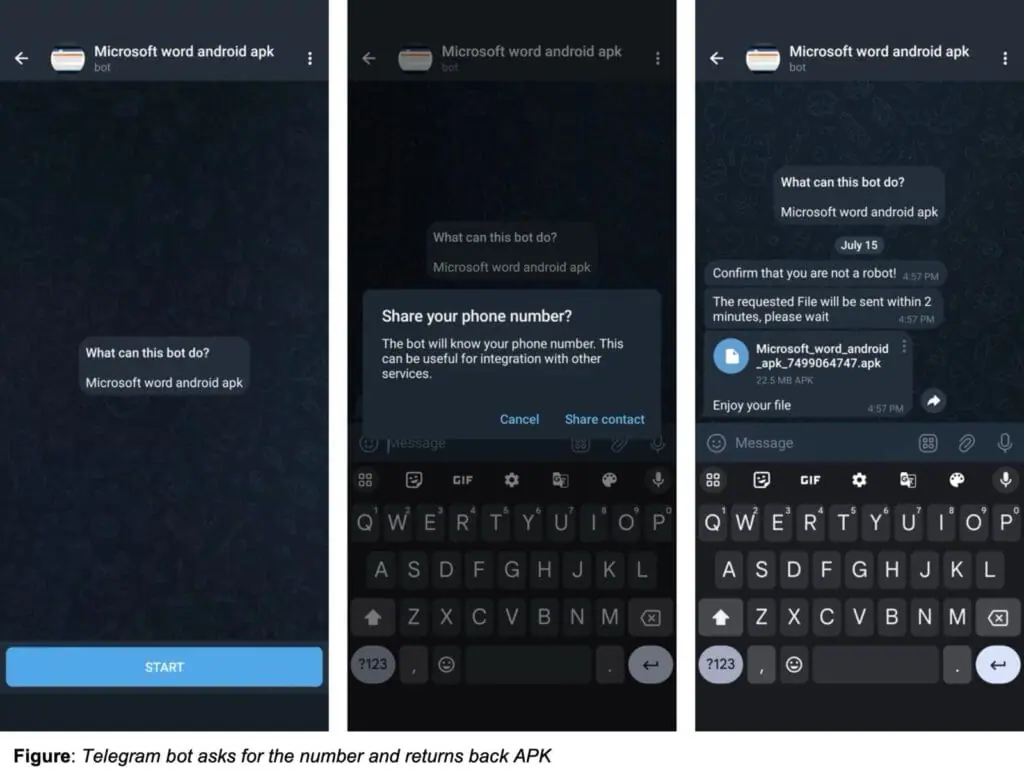
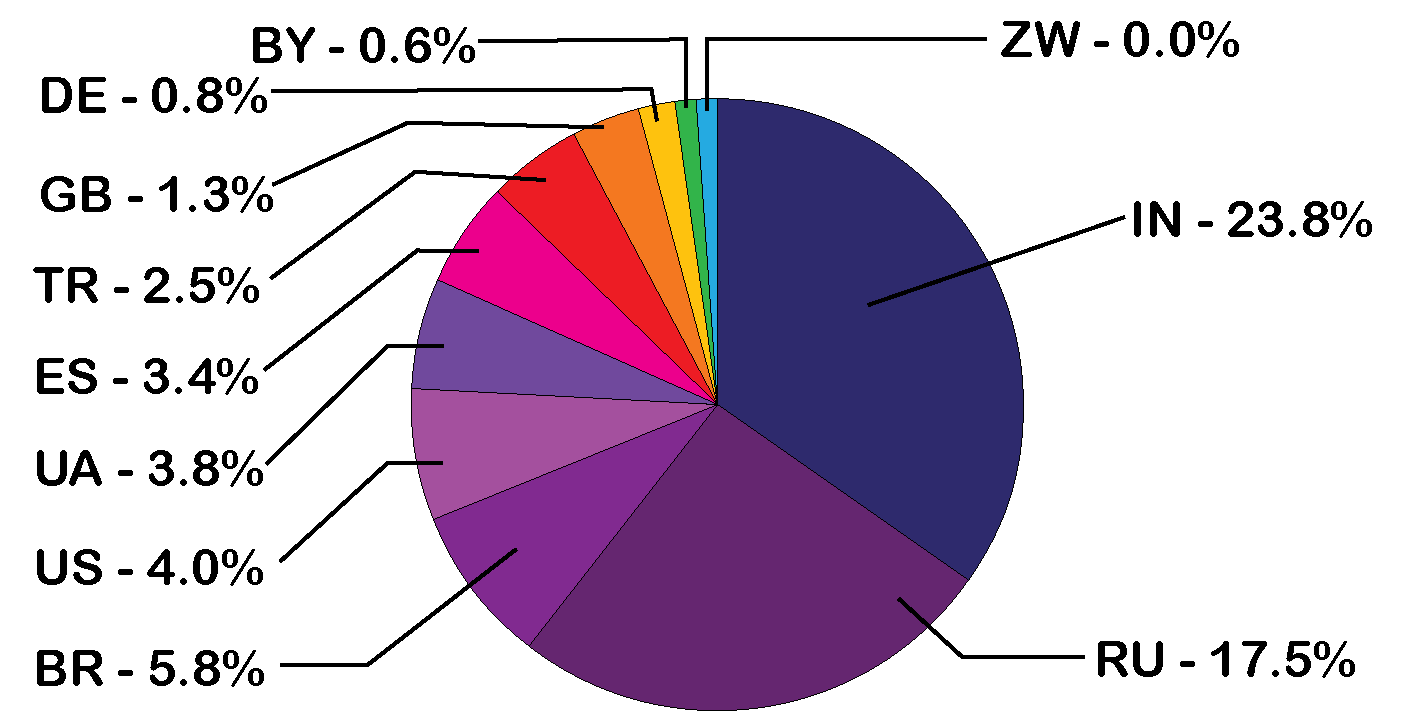
When you turn on Enhanced protection, you’ll receive warnings about potentially dangerous sites, downloads, and extensions, even ones Google didn’t previously know about.
When you visit a site, Chrome sends the URL of the site and a small sample of page content, extension activity, and system information to Google Safe Browsing to check if they’re potentially harmful, including in-depth scans of suspicious downloads. Info sent to Google Safe Browsing is only used for security purposes.
If you’re signed in to your Google Account, Safe Browsing protection extends across your Google services by saving this data to your Google Account — for example, Safe Browsing can increase protection in Gmail after a security incident.
Enhanced protection:
- Improves security for you and everyone on the web.
- Warns you if you use a password that’s been compromised in a data breach.
- Doesn’t noticeably slow down your browser or device.